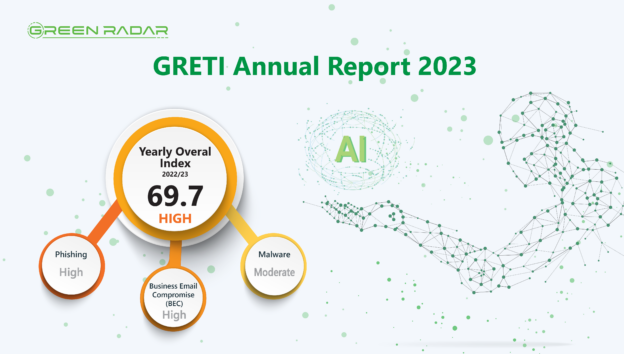
(香港,2024年3月20日)劍達(香港)有限公司(「Green Radar」或「公司」)發佈了最新的電子郵件威脅指數 Green Radar Email Threat Index(「GRETI」或「指數」),作為自 2023 年開始的年度回顧,年度指數顯示為69.7分。指數與上年度的66.5分相比有所增加,反映電郵威脅風險持續上升,應保持警惕。
根據分析,本年度的網絡釣魚(Phishing)和商業電郵詐騙(BEC)攻擊繼續處於「高」風險級別水平。2023 年發生了不少針對政府部門的網絡攻擊,導致數百 GB 的資料遺失和甚至業務資料庫被盜,受入侵的組織被黑客勒索贖金並聲譽受損。當然,事故原因不乏人爲錯誤但系統爲何不堪一擊亦十分值得反思。由此可見,網路釣魚仍是黑客首選的網絡攻擊手法。香港電腦保安事故協調中心(HKCERT)亦在早前公佈在2023年共處理 7,752 宗保安事故,其中網絡釣魚更佔整體個案接近一半(3,752宗,佔48%),對比2022年上升27%,數字創五年新高。與網絡釣魚相關的連結更突破19,000條,相當於每日至少受到52次與釣魚有關的攻擊。
人工智能助長網絡威脅 Quishing攻擊手法有變
根據GRETI的分析,今年預計會有更多利用AI策劃網絡攻擊的情況出現。這是因為AI技術的應用可以幫助犯罪分子生成惡意軟件,同時降低了他們的技術門檻。在新一代的釣魚攻擊中,黑客不僅使用傳統的電郵方式,還運用AI Deepfake技術來冒充他人身份,以贏得受害者的信任,從而詐騙金錢。因此網絡釣魚仍然是最流行的電郵威脅類型,並且在本年度繼續保持上升趨勢;因此企業更需要部署相應的網路釣魚防護解決方案來保護員工和企業免受威脅。
Quishing方面, 黑客用更改了背景顔色和錯誤比例的QR Code 圖片取代以往使用完整QR Code的釣魚電郵,使電郵安全閘道更難透過光學字符識別(OCR) 將這些影像識別為 QR Code。顯示黑客有試圖用不同的Quishing手法攻擊,證明了他們在幕後進行了廣泛的研究工作,以增加網絡釣魚命中率。
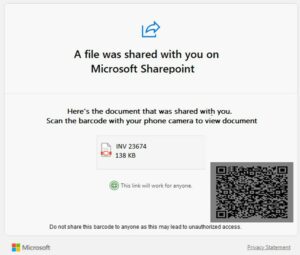
(Quishing 案例示意圖)
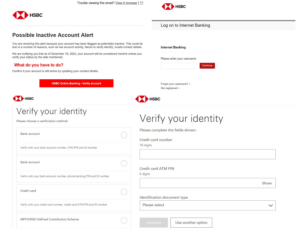
GRETI注意到黑客在設計具針對性的攻擊時,會利用誘餌來吸引收件人的注意。例如假冒受信任和認可的品牌或機構,原因是因為知名品牌在消費者中建立了一定的信任。以SOC攔截到的假冒香港終審法院例子來說,本土化程度高但一般市民大衆收到相關電郵時不免衍生緊張、恐慌的情緒,因此會來不及識別當中的真僞。就這個例子而言,黑客嘗試引導收件人點擊看似正確的文件名稱鏈接並導向其至創建的假網站,務求令網絡釣魚取得成功。
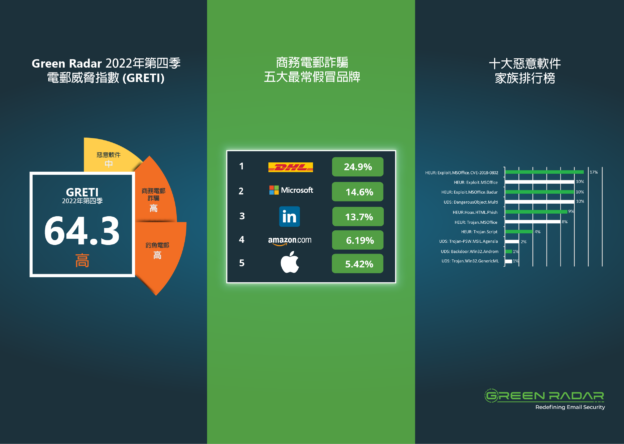
縱觀全年,DHL、WeTransfer、Meta、Spotify和Amazon分列假冒品牌排行榜的前五名。黑客利用假冒知名品牌的策略,透過製作偽造的廣告、促銷活動、優惠等手段,誘使受害者提供個人資訊或進行金錢交易。這些黑客能夠充分利用品牌的信譽、價值和廣泛知名度,從而提高詐騙成功的機會。因此,請保持警惕,仔細驗證其真實性,以免成為黑客的目標。
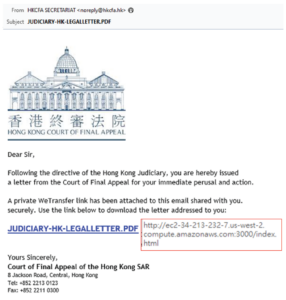
(本土釣魚攻擊例子 – 香港終審法院)
2024年新型網絡釣魚 – 克隆網路釣魚(Clone Phishing)
隨著大家了解到網路釣魚意識培訓的重要性,黑客找到可以繞過培訓並誘騙用戶陷入憑證盜竊的新方法。克隆網路釣魚類似於線程劫持,是一種基於電郵的新型威脅,克隆網絡釣魚會把帶有附件的真實電郵,再假冒原始寄件者重新發送。然後附件被惡意程式替換,但外觀與原始文件相似,因此很難被發現。
注意,克隆網路釣魚並不總是透過電郵回覆的方式進行而是取決於您的業務方式。有時,攻擊是通過複製一封已知企業發送的電郵並將合法的電郵副本發送給目標收件人。由於克隆網路釣魚通常是從合法電郵地址發送,因此無論是否有適當的網路安全措施來阻止,該電郵也會傳遞到使用者的收件匣中。而這封惡意電郵可能附帶勒索軟件或其他任何形式的惡意附件,用於竊取數據。
Green Radar服務運營執行副總裁李祟基先生表示:「網路釣魚攻擊可以透過不同的媒介進行,其中最常見的是電郵。攻擊目的是竊取憑證以接管帳戶,可能導致企業敏感資料外泄和詐欺轉帳等嚴重後果。由於攻擊利用人性弱點,必須防止員工成爲潛在漏洞。員工教育固然重要,但遠距工作和大量郵件和訊息處理使辨識複雜攻擊更困難,因此使用合適的網路釣魚防護解決方案至關重要。」
如欲了解更多電郵威脅最新趨勢,歡迎點擊以下網站下載 GRETI 完整報告:
March 20, 2024, Hong Kong – Green Radar (Hong Kong) Limited (“Green Radar” or “the Company”) has released the latest Green Radar Email Threat Index (“GRETI” or “the Index”), as part of the annual review since 2023. The index for 2023 reached 69.7, indicating a further increase in email threat risks compared to the previous year’s index of 66.5. This highlights the importance of maintaining vigilance in addressing these threats.
According to the analysis, phishing and Business Email Compromise (BEC) attacks continue to pose a “high” level of risk this year. In 2023, numerous cyberattacks targeted government departments resulted in the loss of hundreds of gigabytes of data and even theft of business databases. The compromised organizations were subsequently blackmailed for ransom, leading to reputational damage. While human errors contributed to these incidents, the weaknesses in the systems are also worthy of reflection. Consequently, phishing remains the preferred method for hackers in cyberattacks.
The Hong Kong Computer Emergency Response Team Coordination Centre (HKCERT) recently reported handling a total of 7,752 security incidents in 2023, with phishing accounting for nearly half of the cases (3,752 cases, or 48%), representing a 27% increase compared to 2022 and reaching a five-year high. The number of links associated with phishing exceeded 19,000, equivalent to at least 52 phishing-related attacks per day.
Artificial intelligence fuels cyber threats; Quishing attack techniques have improved
According to GRETI’s analysis, it is expected to see an increase in cyberattacks using AI this year. This is because the application of AI technology can assist criminals in generating malicious software with lowered technical barriers. In the new generation of phishing attacks, hackers not only use traditional email methods but also apply AI Deepfake technology to impersonate others and gain the trust of victims in order to defraud them for money. Therefore, phishing remains the most prevalent type of email threat and continues its upward trend this year. As a result, businesses need to deploy corresponding anti-phishing solutions to protect their employees and organizations from these threats.
Regarding Quishing, hackers have employed a new technique by modifying the background color and using an unusual ratio of QR code images in phishing emails. This approach replaces the previous method of using complete QR codes. By doing so, hackers make it more challenging for email security gateways to recognize these images as QR codes through Optical Character Recognition (OCR). The fact that hackers are attempting to use various Quishing techniques demonstrates their extensive research efforts behind the scenes, aimed at increasing the success rate of their phishing attacks.
GRETI has observed that when hackers design targeted attacks, they use bait to attract the attention of recipients. For example, they may impersonate trusted and recognized brands or institutions, as well-known brands have established a certain level of trust among consumers. Taking the example of a fake Hong Kong Court of Final Appeal email intercepted by our Security Operations Center (SOC), the high level of localization may cause anxiety and panic among the general public when they receive such emails, making it difficult for them to identify the authenticity. In this case, hackers attempt to guide the recipient to click on a seemingly legitimate file name link that redirects recipient to a fake website that hackers created to execute the phishing attack successfully.
Throughout the year, DHL, WeTransfer, Meta, Spotify, and Amazon have consistently ranked among the top five counterfeit brands. Hackers utilized the strategy of impersonating well-known brands by creating forged advertisements, promotional campaigns, and offers to lure victims into providing personal information or engaging in financial transactions. Hackers took advantage of these brands’ reputation, value, and widespread recognition, thereby increasing the chances of successful fraud. Therefore, it is essential to remain vigilant and carefully verify the authenticity of any communication or offer to avoid becoming a target for hackers.
2024 New type of phishing attack – Clone Phishing
Despite the growing awareness of phishing and the importance of cybersecurity training, hackers have found a new method to bypass training and deceive users into falling for credential theft.
Clone Phishing, similar to thread hijacking, is an email-based threat where a genuine email with attachments is cloned and resent, impersonating the original sender. The attachments are then replaced with malicious programs that closely resembled the appearance of the original files, making them difficult to detect.
It is important to note that Clone Phishing doesn’t always occur through email replies but depends on your business practices. Sometimes, the attack involves duplicating an email sent by a known company and sending a legitimate copy to the targeted recipient. Since Clone Phishing often originates from legitimate email addresses, the emails can bypass proper network security measures and land in the users’ inboxes. These malicious emails may contain ransomware or any other form of malicious attachment aimed at stealing data.
Mr. Francis Lee, Executive Vice President, Service Operations at Green Radar, stated, “Phishing attacks can occur through various mediums, with email being the most common among them. These attacks aim to steal credentials to take over accounts, which can result in severe consequences such as the leakage of sensitive corporate data and fraudulent transfers. As these attacks exploit human vulnerabilities, preventing employees from becoming potential vulnerabilities is crucial. While employee education is important, the challenges posed by remote work and handling a large volume of emails and messages make it more difficult to identify sophisticated attacks. Therefore, it is essential to utilize appropriate phishing protection solutions.”
For more email threat updates, please click to download 2023 GERTI Annual Report: