(Hong Kong, 26 July 2022) Green Radar (Hong Kong) Limited (“Green Radar” or “Company”) has released the Green Radar EmailThreat Index (“GRETI” or “Index”) as an annual review since its inauguration release in June 2021, including data for the second quarter of 2022 together. The annual Index is 66.5, while the Q2 index was 68.1. The quarterly index of 68.1 reflects that email threat concern has grown in significance in comparison with last quarter’s 67.4, and a huge surge from last June’s 63.
According to our analysis, phishing and Business Email Compromise (BEC) continues be ‘high’ risk category during the period. Although malware attachments, phishing emails and BEC are all seen to be on an upward trend over the period, threats from malware attachments are considered ‘moderate’ relatively due to the maturity of countermeasures and its evolution trends.
The annual report shows that malicious email campaigns are being tailored and make greater use of catchphrases impersonating local brands, and are designed to extract recipients’ reaction more successfully. They are also being made to be simple to respond to, by introducing new techniques such as QR codes within the message body.

The threat from malicious email activities remains high
According to the GRETI 2021-22 statistics, 56.9% of Hong Kong end users experienced an increase in malicious email activities since June 2021, with an average of 2 phishing attacks per day. For the origins of attacks, United States at 39.4% is the largest location source of malicious email attacks, it is alarming that locally initiated attack forms almost 10% of the total. The report also reveals that most of the email attacks targeted the largest (>1,000) and smallest (<100) organisations in terms of staff number, which the hackers may see them more worthy of attacks.
In addition, Green Radar data shows that Business Email Compromise (BEC) is gaining traction as a favoured method of attack. Hackers are getting more refined and focused on their potential victims, with more tailored attacks aimed for either easy but immediate, or substantial but longer-term returns.
According to the report, phishing remains the most popular type of email threat and continues its upward trend over the period. A significant number of phishing emails we received were designed towards getting recipients’ personal and credit card data, with phishing URL for rewards and refunds. The impersonated local brands the Green Radar Security Operations Center (SOC) has seen include HK Electric, PayMe, Hang Seng Bank, HSBC, MTR, Inland Revenue Department etc.
The SOC statistics shows that malware accounts for 28.15% of all email attacks, with Exploit.MSOffice being the most frequently spread malware. Once infected, documents could exploit vulnerabilities in Microsoft Office software to carry out malicious activities subsequently. In reviewing the nature of these malwares, the most popular family is the Trojanware family, taking the 2nd and 3rd most spread malware spots, accounting for 33% of all malwares detected. This is a class of malware that monitors the activities of the infected system to gain access to it.
Locally tailored and initiated malicious emails attacks
Malicious actors are putting in more efforts to impersonate local brands for successful phishing campaigns. In the past, brands impersonated were more international, such as DHL, LinkedIn and Microsoft. These are perceived to be less threatening because, while being familiar, they would be less likely to resonate with local users. However, HSBC and Hang Seng have become the latest favourites of hackers, being the most impersonated brands towards the 2nd half of the period. These two brands are closer to home as many local users would consider regular communication with these brands to be the norm rather than odd exceptions.
Aside from the named brands, we should also be aware of the increasing manipulation of local well-known brands. PayMe, with its increasing popularity and as a tool to handle government issued Consumer Vouchers, was also exploited. Inland Revenue Department would certainly compel recipients to respond under pressure and hast, especially during a period of tax revenue normalization.
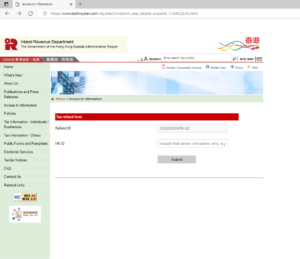
Local phishing case – Inland Revenue Department
As mentioned previously, Green Radar noticed that hackers use local tones when designing customized hacking campaigns, for example, using slogans of local brands as baits to grab the recipients’ attention. Compared with the other impersonated brands, “MTR” is even more localized, and almost everyone can associate MTR with their lives, making reading and reacting to “MTR Reward…” more natural without suspicion. All these references should further enforce the notion of how hackers would make use of local and timely opportunities for the highest success rates and contribute to the ever-higher threat index noted in this quarter.
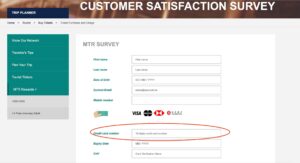
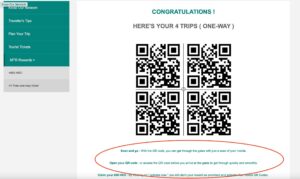
Local phishing case – MTR
Mr. Francis Lee, Executive VP, Product Marketing at Green Radar, commented, “More than 70% of the emails that companies receive every day are spam or malicious attacks. However, the email protection solutions or services on the market are mainly provided by international technology companies, which cannot completely recognise the threat the local businesses are facing. While the attacks are localizing, protection such as email filtering and isolation technologies, should be adjusted to just be as local. More than that, the adoption of threat awareness and related training should take a far more prominent role in cybersecurity policies as it could help corporates to equip staff with enough knowledge and immunity regarding the matter.”
For full report of the “Green Radar Email Threat Index 2021/22 ”, it can be downloaded from: https://greenradar.com/download-report-2021-22-greti-full-report/
