



Securing Privileged Accesses to your critical infrastructure
Critical business data or infrastructures are only accessible to administrators. Getting administrator accounts and passwords allows unrestricted access to all networks and systems. grKey affords extensive granular control of accesses, to balance usage with necessary cyber protection for qualitative governance.
Taking away overheads on costly hardware and software maintenance services, grKey is designed to run from the get-go! Our integrated platform in our MDR allows for our staff to manage the platform on your behalf, while our clients focus on managing the administrators’ credentials and access rights only.
Built on practical enterprise operations and improving upon them, grKey offers more than PAM functionalities, and enhanced with comprehensive life-cycle operation tools including visibility dashboards, granular reporting, exception highlights and remedial functionalities to facilitate daily operational needs.
Visibility and transparency are cornerstones of better governance. grKey is designed with deep insight reporting modules to flexibly gain visibility and reporting into specific aspects of PAM activities, in an extensive, concise and logical manner.
Managing privileged identities require strong operation support and reliable technology platform. Our secured cloud-based platform is designed with this in mind to handle the management of privileged identities in clients’ environments. grKey remotely integrates account management functions, such as password change, user access control and activity visibility with operation support to ensure smooth operation. The platform automatically and regularly updates privileged passwords, rotating expiring, or non-compliant passwords out of use and store them in secured and encrypted data keeps. Operation team ensures that exceptions are handled, as well as driving governance and adaption. This offers a complete Privileged Access Management suite for our clients, while taking away the expensive CAPEX and OPEX to own and run your own operations.
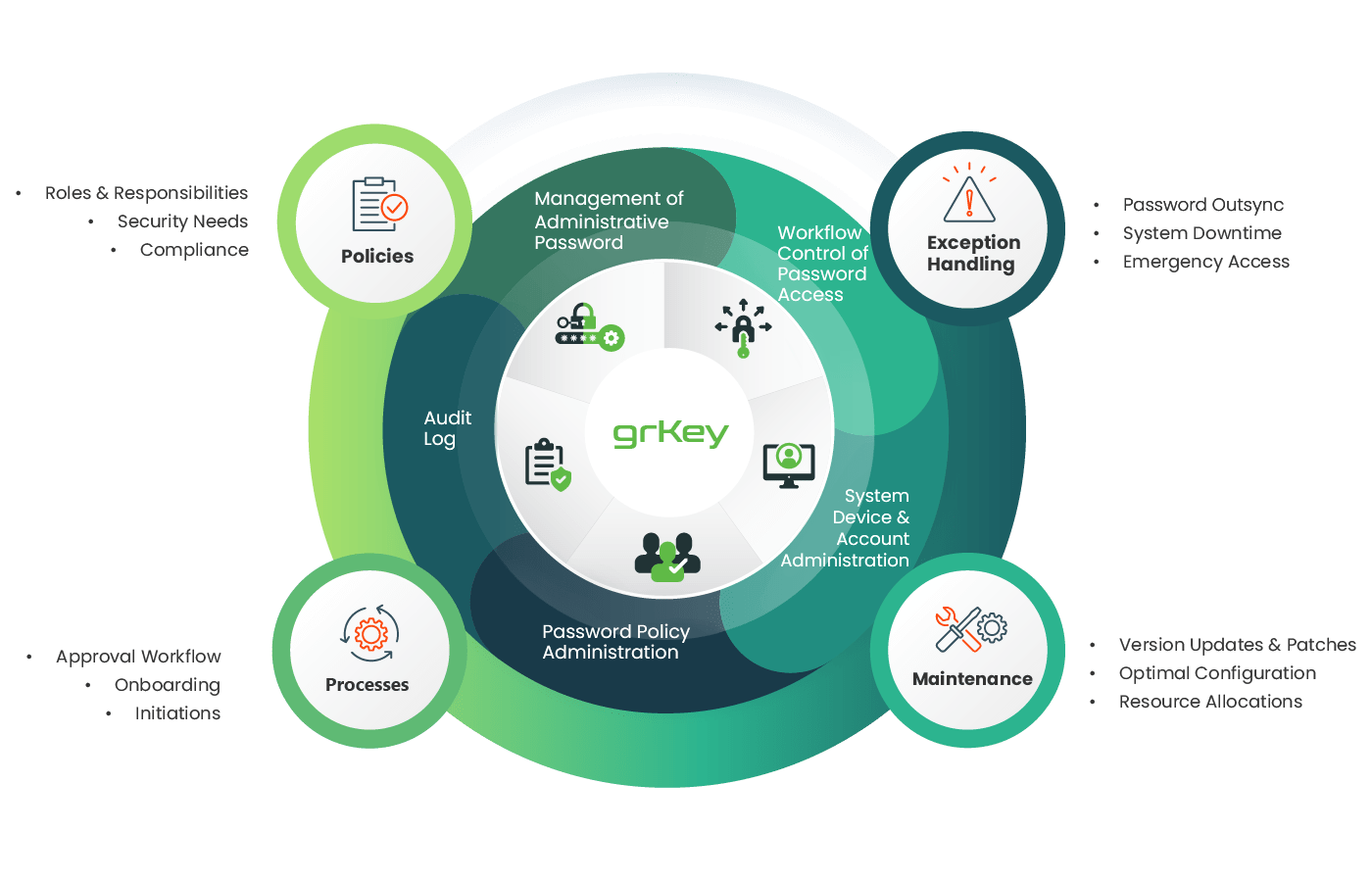
grKey is derived from more than 15 years of extensive PAM operational experiences working with over 200 Hong Kong enterprises, ensuring locally adapted industrial best practices are reflected, as well as addressing shortcomings in existing solutions.
Our technology was built to specifically handle administrative account management. Clients are freed of the most ardent unneeded challenges of owning a PAM solution – its hardware and software maintenances. Our Cloud-hosted PAM is complemented by experienced operational and security teams to ensure stability, and resources are properly governed.
With an existing SOC that had been proven with an uptime of 99.999% and certified to ISO27001. Our team knows how to ensure that service is always available, and that due processes always take place.