(香港,2023年7月25日)劍達(香港)有限公司(「Green Radar」或「公司」)發表 2023 上半年的電郵威脅指數 Green Radar Email Threat Index(「GRETI」或「指數」)。指數顯示為 62.1分(上季為64.3分),反映電郵威脅風險較上季下跌,但風險級別水平維持在「高」。與去年同期相比,Green Radar觀察到每封電郵的整體攻擊量增加了1%,表明整體的攻擊量相對穩定。 然而,實際上的攻擊量絕對增長率增加了86%,這是一個不容小覷的數字也解釋了GRETI指數的下跌。在這個數字中,未知攻擊(Unknown Attacks)/零日攻擊(Zero Day Attacks)與去年同期相比增加了33%。
報告發現,ChatGPT的興起為黑客製作釣魚電郵和假網站提供了便利,使黑客更活躍發動網絡攻擊。加上臨近暑假,黑客看準時機假冒旅游預訂網站騙取信用卡兼個人敏感資料。 Green Radar 的電郵安全監控中心(SOC)攔截了不少相關的釣魚電郵,大部分以信用卡使用情況有「可疑」為由釣魚。

LinkedIn成最常假冒品牌第一 DocuSign首次上榜
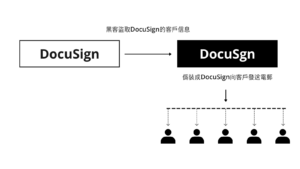
根據上半年的GRETI 數據,商業電郵詐騙(BEC)攻擊較上季微跌。Green Radar SOC 統計數據顯示最常被冒充的三大品牌包括:LinkedIn、微軟和恆生銀行;排行第四和五的分別是Facebook和DocuSign。相信Facebook榜上有名大家已見慣不怪,而第一次出現的DocuSign很值得留意。DocuSign成立於2003年,是一家來自美國的電子簽名服務提供商,提供基於雲的電子簽名平台,幫助企業或用戶在線上快速創建並獲取合法有效的電子簽名。黑客利用非法手段竊取其客戶電郵地址後,偽造了一個假域名“DocuSgn”(比DocuSign少一個字母i),並偽裝成財務部門的發票向用戶發出惡意電郵,由於郵件標題及內容均使用DocuSign的品牌標識,輕易獲取了用戶信任。因此用戶一不留神便被誘使點擊含有惡意代碼的word文檔。如沒有強大的電郵保安措施,企業的内部資料會輕易受到黑客攻擊,造成損失。
(黑客假冒DocuSign示意圖)
十大惡意軟件家族排行榜的第一位是HEUR:Hoax.HTML.Phish,第二位是HEUR:Exploit.MSOffice,HEUR:Exploit.MSOffice.CVE-2018-0802則排行第三位,表示這類軟件頗受黑客歡迎,需要多加留意。
黑客看準時機設計釣魚陷阱
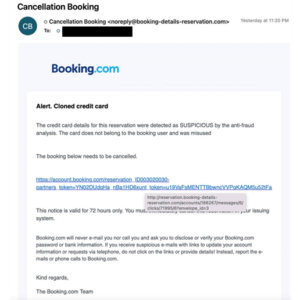
疫情放緩加上旅游業復蘇,黑客看準時機假冒旅游預訂網站向其客戶發送釣魚電郵。根據 SOC提供的booking.com釣魚案例可見,黑客透過盜取用戶的網絡交易資料假冒「網站」以信用卡使用情況有「可疑」並會取消預訂為由實施釣魚詐騙。黑客善於操縱心理,利用用戶收到電郵後的不安情緒逐步讓對方落入自己所設下的陷阱,誘使收件人點擊假網站的連結以盜取其個人及信用卡資料;黑客在電郵中提到「此通知將在72小時後失效」和「booking.com不會向您發送電郵或……驗證你的賬戶密碼或銀行信息」等字眼獲取信任和增加迫切性。只要小心閲讀,便會發現電郵内容是自相矛盾的,一方面讓用戶點擊連結一方面提醒切勿點擊連結。
在此提醒大家在點擊任何連結前請三思,因爲很可能在幾秒鐘的時間内識別到黑客的漏洞從而避免損失。所以,了解釣魚威脅並進行適當的釣魚意識評估和演習必不可少,尤其是當黑客針對性地向企業出擊,提早預防可以消除潛在威脅,大大減少資料外洩、勒索程式及詐騙的風險。Green Radar的grMail 和grAssessment(釣魚意識演習)可為企業提供最適切的電郵解決方案,增加員工對電郵威脅的了解,成爲你企業的把關者。
(黑客假冒booking.com的釣魚電郵例子)
Green Radar 服務營運執行副總裁李祟基先生表示:「網絡犯罪活動越趨頻繁,而且ChatGPT的出現無疑為黑客提供便利,只要巧妙運用字眼便可以利用ChatGPT編寫釣魚内容。所以,選用優質的電郵保安服務供應商是保護企業的第一道防綫,强化企業保護屏障。針對未來發展,我們會不斷優化grMail的技術水平,以自家研發的AI(aidarTM)去調整並提升全球及本地威脅情報、監控及攔截能力,緊貼用戶防衛需求。」
如欲了解更多電郵威脅最新情報,歡迎點擊下載 2022 Q4 GERTI:Green Radar_1H 2023 GRETI Press Release_CN
(25th July 2023, Hong Kong)Green Radar (Hong Kong) Limited (“Green Radar” or “Company”) has released the Green Radar Email Threat Index (“GRETI” or “Index”) for the first half of 2023. The index for the first half is 62.1 (the index released for 2022 was 64.3), the index reflects a moderate decrease compared to the last assessment, though the overall risk level remains ‘High’. Compared to the same period last year, Green Radar observes an 1% increase in overall attack volume per email, showing that the overall attack volume is relatively stable. However, in actual terms the absolute increase in attack volume was 86% year on year and is a significant number. Of this volume, the Unknown / Zero Day attacks had increased by 33% vs the same time last year.
The rise of ChatGPT and other AI tools have facilitated hackers to create phishing emails and fake websites more efficiently, thereby lowers the barrier in launching cyber attacks. In another showing of hackers executes timely attacks, to the summer and holiday season promotions were impersonated with fake travel booking emails and websites to defraud credit cards and personal sensitive information. Green Radar’s Email Security Operations Center (SOC) intercepted many related phishing emails, most of which were phishing on the grounds that the credit card usage was “suspicious”.
LinkedIn ranks no. 1 for most impersonated brand, DocuSign on the list for the first tim
According to GRETI statistics in this first half, business email compromise (BEC)attacks recorded a slight decrease over the same period last year. Though that is not to say that the threat is lessening, the top three most frequently counterfeited brands include: LinkedIn, Microsoft and Hang Seng Bank, with Facebook and DocuSign being the fourth and fifth respectively. It is no surprise that Facebook is enlisted, but DocuSign which debuted on the list is worth noting. Founded in 2003, DocuSign is an electronic signature service provider from the United States. It provides a cloud-based electronic signature platform to help enterprises or users quickly create and obtain legal and valid electronic signatures online. Hackers used illegal means to steal their customers’ email addresses, forged a fake domain name “DocuSgn” (one letter i less than DocuSign), and disguised themselves as invoices from the financial department to send malicious emails to users. Using DocuSign’s brand identity, it is easy to gain the trust of users. Therefore, users are tempted to click on the word documents containing malware without paying attention. In the absence of strong email security solution, this could bring loss to enterprises as their internal data could then be easily hacked.
HEUR:Hoax.HTML.Phish ranks first on the list of top ten malware families, with HEUR:Exploit.MSOffice the second. HEUR:Exploit.MSOffice.CVE-2018-0802 places third. Such ranking indicates that the software is popular among hackers and enterprises should pay more attention to it.
Hackers saw the right time to design phishing traps
With the easing of the epidemic and the recovery of tourism, hackers took advantage of the upsurge to send phishing emails to customers by impersonating travel booking websites. In the phishing case of booking.com, hackers defraud users of their online transaction information and impersonate “websites” to carry out phishing scams, claiming that the credit card usage was “suspicious” and the reservation would be cancelled. Riding on mental manipulation and users’ anxiety after receiving these emails, hackers induce users to fall into their trap gradually by luring recipients to click on fake website links to steal their personal and credit card information. “This notice will be expired in 72 hours” and “booking.com will not send you an email or… verify your account password or bank details” are used to gain trust and add urgency.
Users should be viligent when responding over any links. It is essential to understand phishing threats and conduct appropriate awareness assessment training for enterprises, who with its ample staff of different levels of cyberthreat awareness are prime targets for hackers and potential returns high and worthwhile. Early preventions can eliminate potential threats and greatly reduce the risks of data leakage, ransomware, and financial frauds. Green Radar’s grMail and grAssessment (phishing assessment services) can provide enterprises with the most appropriate email security solutions, increase employees’ understanding of email threats, and become the gatekeepers of your enterprises.
Mr. Francis Lee, Executive Vice President, Service Operations at Green Radar, said, “Cybercrime activities are becoming more and more frequent. The emergence of ChatGPT undoubtedly facilitates hackers by writing phishing content, as long as they weigh their words skillfully. Choosing a professional email security service provider with good quality builds the first line of defense to protect the enterprises and strengthen their protection barriers. For future development, we will continue to optimise the technical level of grMail, as well as adjusting and enhancing global and local threat intelligence, monitoring and interception capabilities by using our own developed AI (aidarTM), so as to align with users’ needs to defense.”
For more email threat updates, please click to download 2022 Q4 GERTI: Green Radar_1H 2023 GRETI Press Release_EN
