(香港,2022年4月28日)劍達(香港)有限公司(「Green Radar」或「公司」)發表 2022 年第一季度的電郵威脅指數Green Radar Email Threat Index(「GRETI」或「指數」)。第一季指數顯示為 67.4分(上季為65.9分),反映電郵威脅風險持續上升並處於高水平。根據分析,這季的網絡釣魚和商業詐騙電郵尤其活躍,因此風險級別水平保持為「高」。今季報告亦發現,近期備受世界關注的「俄烏戰爭」和香港第5波疫情均成爲黑客的釣魚目標,由於事件被熱烈關注,大眾有機會忽略其真確性而成爲黑客的囊中物 。
DHL 穩守第一 Facebook上榜
根據今季GRETI 報告,商業電郵詐騙攻擊比上季大幅增加16.3% 至52.5%。 Green Radar電郵安全監控中心(SOC)統計數據顯示,最常被冒充的三大品牌包括:DHL 、LinkedIn和微軟,排名與上季相同。另外, Facebook首次入選五甲,相信與黑客活躍於Facebook的商業詐騙活動有關。根據SOC攔截的電郵,今年一月至三月有不少聲稱為烏克蘭籌款的商業電郵詐騙,黑客利用俄烏戰爭誘騙用戶向烏克蘭捐款,甚至提供加密貨幣錢包進行交易,從而竊取個人資料及金錢,企業也受到潛在病毒攻擊的威脅。
十大惡意軟件家族排行榜的第一位是UDS:DangerousObject.Multi,HEUR:Exploit.MSOffice.CVE-2018-0802從上季的第六位躍升為第二位,HEUR:Trojan.MSOffice.Emotet則排名第三位。 SOC 同時發現名為Sunseed的惡意軟件,以歐洲政府為目標,收集有關烏克蘭難民去向和針對俄羅斯政府的重要情報。
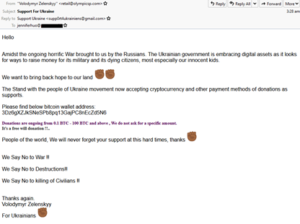
(Green Radar SOC 攔截的俄烏戰爭釣魚郵件)
QR Code揪出Quishing背後隱憂
香港受到疫情影響,市民為減少在日常生活中互相接觸而增加使用流動支付。商戶把QR code(二維碼)用於收款和宣傳上,例如將公司和宣傳品的網址、聯絡方法或地址轉存為QR code,以增加宣傳效果;餐飲業使用QR code作自助點餐亦變得普遍;可見使用QR code漸趨普及。而網絡釣魚電子郵件中使用的QR code被稱為「Quishing」,當用戶掃瞄QR code後,便會進入釣魚網站。
據SOC提供的數據顯示,2022年首季的網絡釣魚攻擊激增30.2%,「Quishing」是結合QR code獨特性+Phishing的攻擊。而透過分析近期的「Quishing」,我們得知黑客透過創新手段,輕鬆繞過電子郵件網關和電腦安全控制中存在的電郵附件的 URL 掃描功能。有美國的網絡保安公司在2021年9月進行過釣魚攻擊演練, 透過釣魚郵件附帶一個音檔。但在這次演練中,電郵安全系統成功偵測該檔案並確認為威脅。有趣的是,該公司一個月後重施故技, 釣魚郵件只附帶了QR code,最後卻成功通過保安措施。由於QR code是一個圖像,不能像點擊連結或打開附件一樣直接觸發攻擊,而現有的保安系統未必能識別為一個威脅,或能成功繞過安全偵測,攔截上有一定困難,因此「Quishing」可能是日後一種攻擊新常態。


(Green Radar SOC在2020年已攔截過類似案例)
Quishing可致什麽損失?
SOC 提醒 ,一旦用戶不慎掃瞄在假冒網站的QR code,賬戶會輕鬆被黑客控制導致資料外洩。網絡釣魚攻擊手法推陳出新,「Quishing」作為在惡意攻擊前的嘗試時十分有效,因為標準的電郵安全保護(如 URL 掃描)無法在郵件中探測到任何可疑連結或附件,從而讓看似正常安全的電子郵件能成功獲取受害者的信任。
Green Radar 銷售執行副總裁馬偉雄表示:「香港第5波疫情的網絡攻擊大幅增加是預料之中,網絡犯罪對黑客而言是一個有趣並且賺錢的遊戲,因此他們樂此不疲。而隨著企業和員工越來越有安全意識,黑客也會調整他們的策略尋找漏洞。為保障企業安全,緊貼行業的威脅情報成為了最重要的資訊,Green Radar不斷在電子郵件安全和安全意識培訓方面為整個行業及客戶作出努力,務求取得最新情報,助企業解決未知的威脅。」
如欲了解更多電郵威脅最新情報,歡迎點擊下載 2022 GERTI Q1:https://bit.ly/3F1tI0x
(Hong Kong, 28 April 2022) Green Radar (Hong Kong) Limited (“Green Radar” or “Company”) released the Green Radar Email Threat Index (“GRETI” or “Index”) for the first quarter of 2022. The Q1 Index scored 67.4, as compared with last quarter’s 65.9, reflected the email threat remained as an imminent risk and was ever growing. According to our analysis, the especially robust phishing and business email compromise (BEC) remained the ‘high’ risk ratings during the period. The quarterly report also reveals that the recent world events including the Russian-Ukrainian conflict and the fifth wave of COVID-19 pandemic in Hong Kong have become the topics of phishing emails that trick users who overlooked the email authenticity and fell prey to hackers.
DHL cements its top position on the list as the most impersonated brand and Facebook debuts on the list
According to the GRETI 2022Q1 Report, BEC attacks leaped from 16.3% last quarter to 52.5% this quarter. Green Radar Security Operations Center (SOC) statistics showed that the top three most impersonated brands are DHL, LinkedIn and Microsoft, which are the same as last quarter. On the other hand, Facebook debuted on the top five list which can be explained by the increased BEC attacks through Facebook. According to the emails intercepted by the SOC, a significant portion of BEC attacks was launched in the name of fundraising campaign for Ukraine, deceived the victims to donate for the country under siege by using their cryptocurrency wallets which would then be compromised for personal credentials and money loss. Corporates were also exposed to similar potential malicious threat.
UDS:DangerousObject.Multi ranked first among the top ten malware families, while HEUR:Exploit.MSOffice.CVE-2018-0802 jumped to the second place from sixth in last quarter, it was followed by HEUR:Trojan.MSOffice.Emotet. SOC also identified Sunseed, a malware targeting European Governments which gathers the whereabouts of Ukrainian refugees and important intelligence that relate to the Russian Government.
Quishing: The hidden threat behind QR Code Scanning
Shadowed by the pandemic, Hong Kong people increases mobile payment usage to avoid physical contact in our daily life. Merchants tend to make use of QR codes (2 dimensional code) for the payment and promotion purpose by converting their website URLs, hyperlinks of their marketing materials, contact information or addresses to maximize visual effect. The automated ordering process at restaurants has become more common these days, which made QR code more popular. “Quishing” is a tactic that apply QR code in phishing attack, users will enter phishing websites by scanning malicious QR codes.
The statistics of the SOC, showed an increase of 30.2% in phishing attacks. “Quishing” combines the uniqueness of QR code to make successful phishing attacks. By analysing the recent “Quishing” incidents, we learnt that innovative hackers are bypassing email security gateways and the URL scanning feature of PCs’ security gate. An U.S.-based cybersecurity company conducted a phishing assessment in September 2021 by sending an audio file in a phishing email, which was identified as a threat by the email security system. Interestingly, they successfully bypassed the security gate with another phishing email with QR code they sent one month later. This gives rise to “Quishing” as a new favourite hacking tactics given that QR code is solely an image that cannot trigger immediate attacks like hyperlink nor a malicious attachment, therefore, it becomes more challenging to identify as a threat by existing email security system.
Potential Threat of Quishing
SOC warns incautious scan on the QR code of phishing websites could provide hackers opportunity to compromise your personal accounts easily and lead to personal credentials leakage. With the fact that phishing technique is evolving, “Quishing” is a highly effective exploit tactics prior to actual malicious attack, as it is different nature compared with standard email protection (for instance, URL scan).
Mr. Kenneth Ma, Executive Vice President of Sales at Green Radar, commented, “It is expected that the significant increase of email attacks leveraging the fifth wave of COVID-19 pandemic in Hong Kong. Cyber criminals profit tirelessly from their so-called mind game to trick users. Following the increasing security awareness of enterprises and their staff, hackers plan their strategies ahead and exploit new loopholes. It is therefore essential for companies to keep updated on the latest threats nowadays. Green Radar continues its dedication to email security and staff awareness training as a part of effort to contribute to the industry and clients as a whole, and aim to tackle unknown threats for corporates with the valuable threat intelligence.”
For more email threat updates, please click to download 2022 GERTI Q1: https://bit.ly/3y27Y3t
